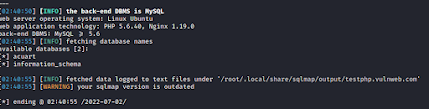
SQL Injection Full tutorial with Example to dump Data.

SQL Injection (SQLi) Overview SQL injection may occcur when user or attacker controlled input is later incorporated into an SQL query which is built and executed by the web application. Web applications which do not implement code-data segmentation by using routines (i.e. - stored procedures, user-defined functions) may be vulnerable. Some sites attempt to parameterize queries which prevents SQL injection but fails to meet other objectives such as least-privilege. Discovery Methodology Inject all available parameters of the web page with charaters reserved in SQL, PL/SQL, T-SQL, and MySQL. Examine responses for difference from responses with normal input. Additionally attempt to inject valid SQL statements including statements which cause errors, induce pauses, and cause differences when similar statements evaluate to true or false. Hint: Use Burp-Suite and SQLMap to fuzz sites quickly Exploitation Determine the prefix and suffix needed to make the i...